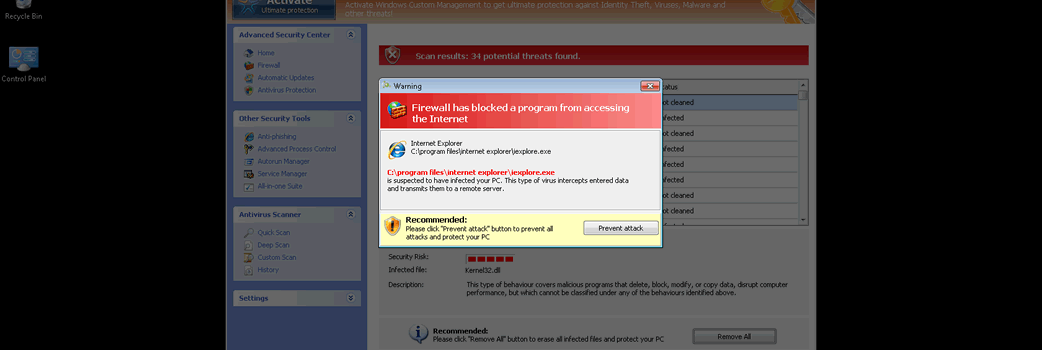
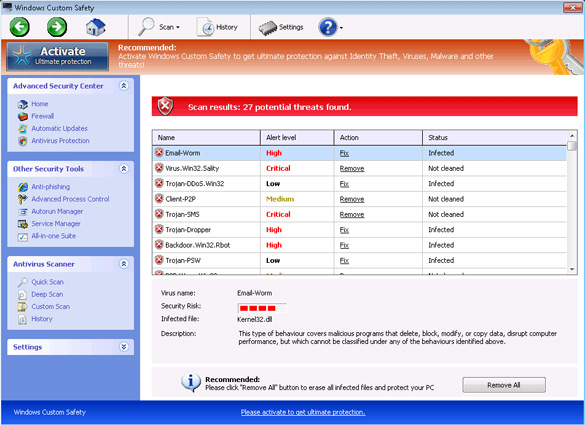
Windows Custom Safety is a fake security program or what some may refer to as being a rogue antispyware application. Windows Custom Safety purports the ability to detect and remove malware from a PC. From the looks of Windows Custom Safety’s interface, it seems to have what it takes to complete such promises. Unfortunately, everything about Windows Custom Safety is a ploy and scam to get PC users to buy a registered copy of Windows Custom Safety. Even the registered copy of Windows Custom Safety is a fake.
PC users who have had the unfortunate situation of having Windows Custom Safety installed on their PC, are not able to easily remove it from their computer. Basically, Windows Custom Safety cannot be uninstalled utilizing the Windows control panel. Being this way, Windows Custom Safety can only be removed through a complicated manual process or utilizing an updated antimalware application. In using an antimalware program, Windows Custom Safety can be safely detected and removed.
How Can You Remove Windows Custom Safety?
Windows Custom Safety can be very difficult to manually remove if you are an inexperienced computer user. Not to mention, Windows Custom Safety has been known to populate the Windows Registry with many different entries and removing the wrong entries could render a PC damaged or useless. The use of a reputable antispyware or antivirus tool is recommended to safely remove Windows Custom Safety from your Windows computer.
To easily remove Windows Custom Safety, find the following process and end them in the task manager. After that is done, delete each related Windows Custom Safety file from your hard drive. In additional to locating the following processes, it is recommended that you delete the Windows Custom Safety registry entries listed below as well. It is also a good idea to uninstall the Windows Custom Safety application via your add/remove programs function found in the Windows Control Panel if your system recognizes Windows Custom Safety has an installed program.
Windows Custom Safety files (and folders) to remove:
- %AppData%\Protector-[RANDOM CHARACTERS].exe
Windows Custom Safety registry entries to remove:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\About.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ackwin32.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alogserv.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe\”Debugger” = “svchost.exe”
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector = %AppData%\Protector-[RANDOM CHARACTERS].exe
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\a.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ad-Aware.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentsvr.exe\”Debugger” = “svchost.exe”
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe\Debugger = svchost.exe
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentw.exe\”Debugger” = “svchost.exe”