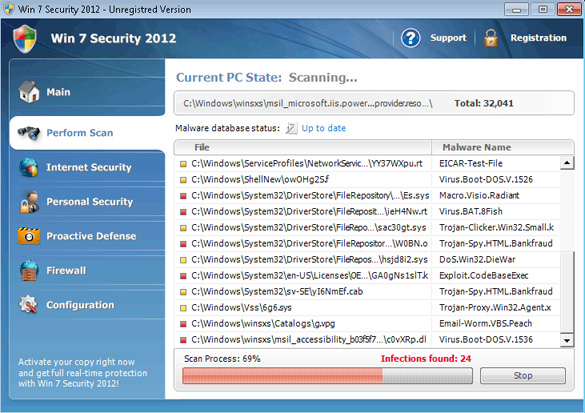
Win 7 Security 2012 has been running amuck the internet basically terrorizing PC users through a series of endless pop-up alerts and system scan notifications. These messages and pop-up alerts coming form the Win 7 Security 2012 program have been found to be bogus. Better yet, the Win 7 Security 2012 application has been determined by several PC security resources as a fake anti-spyware program.
Win 7 Security 2012 is among a long list of plagiarized security applications for the PC. It is one that utilizes the similar naming of the latest Windows operating system, Windows 7, to gain the trust of a multitude of computer users. Even still, Win 7 Security 2012 looks as if it is part of the Windows 7 operating system from its colors and cleverly designed interface. If a computer user trusts Win 7 Security 2012 enough, then they could end up purchasing Win 7 Security 2012 in order to remove the so-called threats that it detected on their PC. To be honest, these threats are really fabricated. Additionally, Win 7 Security 2012 is not able to remove any type of legitimate threat, virus or other PC malware even if the so-called ‘purchased version’ of Win 7 Security 2012 is used.
How Can You Remove Win 7 Security 2012?
Win 7 Security 2012 can be very difficult to manually remove if you are an inexperienced computer user. Not to mention, Win 7 Security 2012 has been known to populate the Windows Registry with many different entries and removing the wrong entries could render a PC damaged or useless. The use of a reputable antispyware or antivirus tool is recommended to safely remove Win 7 Security 2012 from your Windows computer.
To easily remove Win 7 Security 2012, find the following process and end them in the task manager. After that is done, delete each related Win 7 Security 2012 file from your hard drive. In additional to locating the following processes, it is recommended that you delete the Win 7 Security 2012 registry entries listed below as well. It is also a good idea to uninstall the Win 7 Security 2012 application via your add/remove programs function found in the Windows Control Panel if your system recognizes Win 7 Security 2012 has an installed program.
Win 7 Security 2012 files (and folders) to remove:
- %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]
- %AppData%\Local\[RANDOM CHARACTERS]
- %Temp%\[RANDOM CHARACTERS]
- %AppData%\Local\[RANDOM CHARACTERS].exe
- %AllUsersProfile%\[RANDOM CHARACTERS]
Win 7 Security 2012 registry entries to remove:
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%Program Files%\Mozilla Firefox\firefox.exe”‘
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%Program Files%\Mozilla Firefox\firefox.exe” -safe-mode’
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%Program Files%\Internet Explorer\iexplore.exe”‘
- HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1″ %*’
- HKEY_CLASSES_ROOT\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “IsolatedCommand” – ‘”%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “(Default)” = ‘”%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon “(Default)” = ‘%1″
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “IsolatedCommand” = ‘”%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\exefile “Content Type” = ‘application/x-msdownload’
- HKEY_CURRENT_USER\Software\Classes\exefile “(Default)” = ‘Application’
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “IsolatedCommand” = ‘”%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “(Default)” = ‘”%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon “(Default)” = ‘%1″ = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “IsolatedCommand” = ‘”%1″ %*’
- HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = ‘exefile’
- HKEY_CURRENT_USER\Software\Classes\.exe “Content Type” = ‘application/x-msdownload’